Accessing the Firewall
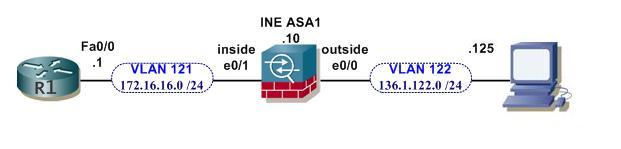
After returning from vacation, Bob (the optimistic firewall technician) decided that he wanted to take some time and get a little bit more familiar with firewall configuration. He was able to get permission to use some spare equipment for practice.
![marvin_9-25[1] marvin_9-25[1]](https://assets.ine.com/blog/images/105b8204-5bf8-4ca6-8831-99291d8268c9.jpg)
He started with a basic configuration on the firewall:
hostname INEASA1
password cisco
enable password ciscointerface e0/1
nameif inside
no shut
ip address 172.16.16.10 255.255.255.0
security-level 90interface e0/0
nameif outside
ip address 136.1.122.10 255.255.255.0
security-level 10
no shut
Bob verified that he could ping both R1 and his PC from the Firewall. Now, he wants to configure the firewall to allow telnet from his PC. He remembers that there was some additional configuration that needed to be done on the firewall to allow this to work, but doesn't remember exactly what is needed. Since his PC isn't connected to the internet, he is not able to access the online documentation.
What additional configuration will allow Bob to telnet to the firewall from his PC?
There is more than one possible solution for this challenge. Feel free to post your proposed answer in the comments section. We will try to keep comments hidden from public view, so that the fun isn't spoiled for others.
____
OK, so let's look at the problem here. The PC is on the outside of the firewall, and according to multiple responses, you can't telnet to the outside interface. (or can you?)
A few helpful hints when studying for the CCIE lab.
1. Don't be afraid to go to the documentation, even for topics you think you know.
2 Re-read the question, to see just what you are asked to do and what your restrictions are.
So, where does the confusion about being able to telnet to the firewall come from? Perhaps it comes from trying in earlier versions, perhaps some confusion about what the documentation says, or perhaps someone read somewhere in the past that it just wouldn't work.
Let's start by carefully re-reading the documentation. ASA - Config guide - system administration - managing system access - allowing telnet
This section states:
"...The security appliance allows Telnet connections to the security appliance for management purposes. You cannot use Telnet to the lowest security interface unless you use Telnet inside an IPSec tunnel. ..."
So, it doesn't explicitly mention the outside, it mentions the "lowest security interface". In most cases that is the outside, but not always.
A few "solutions"
1. Configure the switch so that Bob's PC is on VLAN 121 instead of VLAN 122, configure the firewall to allow telnet on the inside interface. (Technically would meet requirements, but not much of a challenge.)
2. Change the security levels for the interfaces, making them the same or making the outside higher.
3. Add another interface with a lower security level
int eth0/1.1
vlan 123
nameif DMZ
sec 9
4. Configure a VPN for the firewall, so that the telnet traffic to the lower security (outside) interface is encrypted and therefore allowed.
5. Configure the firewall to allow transit traffic through to R1. Telnet to R1, and then Telnet to the ASA from R1, after configuring the ASA to allow telnet on the inside interface.