25 November 09
CCIE Security Core Knowledge Questions - Part 3
Posted byINE
For Part 2 of this series, click here.
The following questions will be added to the Core Knowledge Simulation engine. Answers will be provided in the comments section.
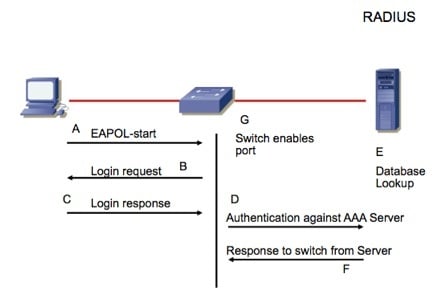
Implement Identity Management
Refer to the diagram. The software running on the PC performs what role?

Configure Cisco IPS to mitigate network threats
Refer to the diagram. How are IPS alerts from the IOS router collected on IME and MARS?

Implement secure networks using Cisco ASA Firewalls
When a new policy-map is applied globally, what effect does that have on the interfaces of the ASA?
Implement secure networks using Cisco VPN solutions
What layer 4 ports / protocols would typically be used as part of a GDOI implementation?