IKE Phase 1 didn't phase you! (And Bob is ecstatic about the help).
In a word, "Way to GO" (without the spaces, that would be one word :) ). I am impressed at all the feedback and ideas we received regarding the IKE phase 1 riddle we posed last week. You can read the original post here. Ideas were creative and varied.
As one of our INE Instructors say, "If there are 2 different ways to configure something, as a CCIE candidate, you had better be prepared to know all 3 ". If you would like to see "a solution", read on.
Ideas sent in included unique identities, isakmp profiles, DMVPN, GETVPN, virtual tunnel interfaces, key-rings, and a few even included full configurations regarding their ideas. Excellent work and effort to all!
So a huge thanks goes out to Nick, Igor, Fedia, Jeff, AJN, MG, Paul A and Paul S! Read below to find out which one of you won the tokens!
There are more than 1 way of solving this IKE challenge. My intention was to assist those getting ready for the lab with the absolute best preparation, and that preparation is practicing it. My feeling is that unless we have gone through the debugs for IKE phase 1, and IKE phase 2, and pushed through the CA authentication and enrollment process, we aren't ready to face the lab. When we are to the point that we can look at the debugs, and say, "Yup, that's the problem, and here's why" that is a good indication we are getting close to ready for that topic.
Here is the solution I put together for this task. I chose what I felt would be a fairly straight forward solution, separating the termination points, logically, for the different sets of traffic, and placing keys and IKE phase 1 policies strategically. One of the items, that I failed to remember while putting this solution together, was to match the EasyVPN group name on the server, with the OU name in the client certificate. I appreciate the opportunity to "remember" and to sharpen my skills too!
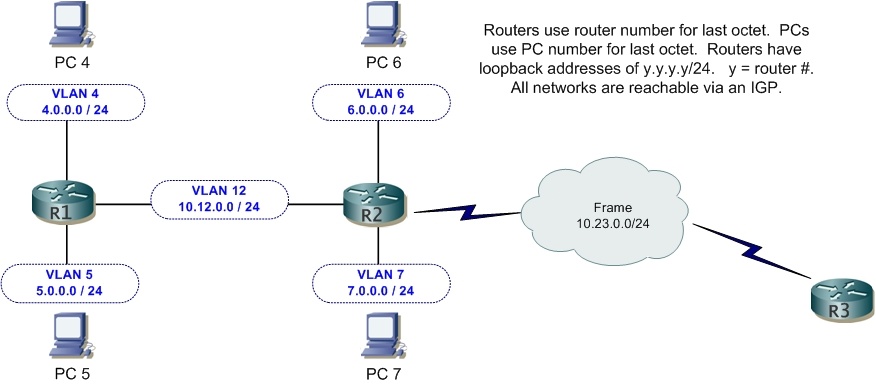
Here is the diagram again. Below it, the final solutions and verifications.

Here are the configurations for the routers, beginning with R1, which is the EasyVPN server. Both R1 and R2 authenticated and enrolled with R3 who acted as a CA server for this IPSec "get-together".
R1#show run brief
version 12.4
hostname R1
!
aaa new-model
!
aaa authentication login Method-2 local
aaa authorization network Method-1 local
clock timezone PST -8
clock summer-time PDT recurring
ip cef
!
no ip domain lookup
ip domain name ine.com
!
crypto pki trustpoint CA-R3
enrollment url http://3.3.3.3:80
fqdn R1.ine.com
subject-name O=ine, OU=vpn_group, CN=R1, C=us, ST=nv
revocation-check none
!
username admin privilege 15 password 0 cisco
!
crypto isakmp policy 1
encr 3des
group 2
!
crypto isakmp policy 2
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 2.2.2.2
!
crypto isakmp client configuration group vpn_group
pool MyPOOL
acl 100
save-password
netmask 255.255.255.0
!
crypto isakmp profile IKE-PROF-1
match identity group vpn_group
client authentication list Method-2
isakmp authorization list Method-1
client configuration address respond
virtual-template 1
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto ipsec profile IPSec-PROF-1
set transform-set ESP-3DES-SHA
set isakmp-profile IKE-PROF-1
!
crypto map MYMAP 1 ipsec-isakmp
set peer 2.2.2.2
set transform-set ESP-3DES-SHA
match address 101
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
!
interface Loopback4
ip address 4.0.0.1 255.255.255.0
!
interface Loopback5
ip address 5.0.0.1 255.255.255.0
!
interface FastEthernet0/0
ip address 10.12.0.1 255.255.255.0
crypto map MYMAP
!
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IPSec-PROF-1
!
router rip
version 2
network 1.0.0.0
network 4.0.0.0
network 5.0.0.0
network 10.0.0.0
no auto-summary
!
ip local pool MyPOOL 4.0.0.51 4.0.0.100
!
!
access-list 100 permit ip 4.0.0.0 0.0.0.255 any
access-list 101 permit ip 5.0.0.0 0.0.0.255 7.0.0.0 0.0.0.255line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
line vty 0 4
privilege level 15
!
ntp authentication-key 1 md5 0822455D0A16 7
! Note: the trusted-key statement isn't needed on the server, but there is a bug
! that on some IOS versions causes to not function if it is not there.
ntp trusted-key 1
ntp source Loopback0
ntp master 5
!
endR1#
What a fun read that was. Now for R2.
R2#show run brief
version 12.4
hostname R2
clock timezone PST -8
clock summer-time PDT recurring
ip cef
!
no ip domain lookup
ip domain name ine.com
!
crypto pki trustpoint CA-R3
enrollment url http://3.3.3.3:80
fqdn R2.ine.com
subject-name O=ine, OU=vpn_group, CN=R2, C=us, ST=nv
revocation-check none
!
username admin privilege 15 password 0 cisco
!
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
crypto isakmp key cisco address 10.12.0.1
!
!
crypto ipsec transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
!
crypto ipsec client ezvpn EZVPN_CLIENT
connect auto
mode network-extension
peer 1.1.1.1
virtual-interface 1
username admin password cisco
xauth userid mode local
!
crypto map MYMAP local-address Loopback0
crypto map MYMAP 1 ipsec-isakmp
set peer 10.12.0.1
set transform-set ESP-3DES-SHA
match address 100
!
interface Loopback0
ip address 2.2.2.2 255.255.255.0
!
interface Loopback6
ip address 6.0.0.2 255.255.255.0
crypto ipsec client ezvpn EZVPN_CLIENT inside
!
interface Loopback7
ip address 7.0.0.2 255.255.255.0
!
interface FastEthernet0/0
ip address 10.12.0.2 255.255.255.0
crypto map MYMAP
crypto ipsec client ezvpn EZVPN_CLIENT
!
interface Serial0/1
no ip address
encapsulation frame-relay
no frame-relay inverse-arp
!
interface Serial0/1.23 point-to-point
ip address 10.23.0.2 255.255.255.0
frame-relay interface-dlci 203
!
interface Virtual-Template1 type tunnel
no ip address
tunnel mode ipsec ipv4
!
router rip
version 2
network 2.0.0.0
network 6.0.0.0
network 7.0.0.0
network 10.0.0.0
no auto-summary
!
access-list 100 permit ip 7.0.0.0 0.0.0.255 5.0.0.0 0.0.0.255
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
line vty 0 4
privilege level 15
no login
!
ntp authentication-key 1 md5 05080F1C2243 7
ntp authenticate
ntp trusted-key 1
ntp clock-period 17179982
ntp server 1.1.1.1
!
endR2#
Let's start the verification process on R1. We will clear the tunnels, and initiate traffic from R2 from network 4 to 6, and then from network 5 to 7. Because R2 is an EasyVPN remote, it will be initiating the tunnel back for the network 6 to 4 encryption with EasyVPN (nothing to to with IPv6 tunnels) :)
R1#clear crypto isakmp
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to down
R1#clear crypto sa
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to up
R1#ping 6.0.0.2 source 4.0.0.1 repeat 15Type escape sequence to abort.
Sending 15, 100-byte ICMP Echos to 6.0.0.2, timeout is 2 seconds:
Packet sent with a source address of 4.0.0.1
!!!!!!!!!!!!!!!
Success rate is 100 percent (15/15), round-trip min/avg/max = 72/179/252 ms
R1#ping 7.0.0.2 source 5.0.0.1 repeat 75Type escape sequence to abort.
Sending 75, 100-byte ICMP Echos to 7.0.0.2, timeout is 2 seconds:
Packet sent with a source address of 5.0.0.1
.!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!
Success rate is 98 percent (74/75), round-trip min/avg/max = 28/154/292 ms
R1#show crypto ipsec sainterface: FastEthernet0/0
Crypto map tag: MYMAP, local addr 10.12.0.1protected vrf: (none)
local ident (addr/mask/prot/port): (5.0.0.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (7.0.0.0/255.255.255.0/0/0)
current_peer 2.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 74, #pkts encrypt: 74, #pkts digest: 74 #pkts decaps: 74, #pkts decrypt: 74, #pkts verify: 74
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0local crypto endpt.: 10.12.0.1, remote crypto endpt.: 2.2.2.2
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xEB4512D2(3947172562)inbound esp sas:
spi: 0xE00894E5(3758658789)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 37, flow_id: SW:37, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4398286/3579)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEinbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xEB4512D2(3947172562)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 38, flow_id: SW:38, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4398286/3579)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEoutbound ah sas:
outbound pcp sas:
interface: Virtual-Access2
Crypto map tag: Virtual-Access2-head-0, local addr 1.1.1.1protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 10.12.0.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 17, #pkts encrypt: 17, #pkts digest: 17 #pkts decaps: 15, #pkts decrypt: 15, #pkts verify: 15
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0local crypto endpt.: 1.1.1.1, remote crypto endpt.: 10.12.0.2
path mtu 1514, ip mtu 1514, ip mtu idb Loopback0
current outbound spi: 0xB923167D(3106084477)inbound esp sas:
spi: 0x44649B73(1147444083)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 35, flow_id: SW:35, crypto map: Virtual-Access2-head-0
sa timing: remaining key lifetime (k/sec): (4575108/3520)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEinbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xB923167D(3106084477)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 36, flow_id: SW:36, crypto map: Virtual-Access2-head-0
sa timing: remaining key lifetime (k/sec): (4575107/3520)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEoutbound ah sas:
outbound pcp sas:
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
1.1.1.1 10.12.0.2 QM_IDLE 1015 0 ACTIVE 2.2.2.2 10.12.0.1 QM_IDLE 1016 0 ACTIVER1#show crypto isakmp sa detail
Codes: C - IKE configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal
X - IKE Extended Authentication
psk - Preshared key, rsig - RSA signature
renc - RSA encryption
IPv4 Crypto ISAKMP SAC-id Local Remote I-VRF Status Encr Hash Auth DH Lifetime Cap.
1015 1.1.1.1 10.12.0.2 ACTIVE 3des sha rsig 2 23:58:18 CX
Engine-id:Conn-id = SW:151016 10.12.0.1 2.2.2.2 ACTIVE 3des sha psk 2 23:59:24
Engine-id:Conn-id = SW:16
R1#
Now we will look at R2, using the same process. Clear the SAs, then send interesting traffic.
R2#clear crypto isakmp
%CRYPTO-6-EZVPN_CONNECTION_DOWN: (Client) User=admin Group= Server_public_addr=1.1.1.1 c
%LINK-3-UPDOWN: Interface Virtual-Access1, changed state to down
R2#clear crypto sa
R2#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to down
R2#
%CRYPTO-6-EZVPN_CONNECTION_UP: (Client) User=admin Group= Server_public_addr=1.1.1.1
R2#
%LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up
R2#
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up
R2#ping 4.0.0.1 source 6.0.0.2 repeat 32Type escape sequence to abort.
Sending 32, 100-byte ICMP Echos to 4.0.0.1, timeout is 2 seconds:
Packet sent with a source address of 6.0.0.2
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 100 percent (32/32), round-trip min/avg/max = 128/171/256 ms
R2#ping 5.0.0.1 source 7.0.0.2 repeat 99Type escape sequence to abort.
Sending 99, 100-byte ICMP Echos to 5.0.0.1, timeout is 2 seconds:
Packet sent with a source address of 7.0.0.2
.!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
Success rate is 98 percent (98/99), round-trip min/avg/max = 16/133/352 ms
R2#show crypto ipsec client ezvpn
Easy VPN Remote Phase: 6Tunnel name : SDM_EZVPN_CLIENT_1
Inside interface list: Loopback6
Outside interface: Virtual-Access1 (bound to FastEthernet0/0)
Current State: IPSEC_ACTIVE
Last Event: MTU_CHANGED
Save Password: Allowed
Split Tunnel List: 1
Address : 4.0.0.0
Mask : 255.255.255.0
Protocol : 0x0
Source Port: 0
Dest Port : 0
Current EzVPN Peer: 1.1.1.1R2#show crypto ipsec sa
interface: Virtual-Access1
Crypto map tag: Virtual-Access1-head-0, local addr 10.12.0.2protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 1.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 32, #pkts encrypt: 32, #pkts digest: 32 #pkts decaps: 35, #pkts decrypt: 35, #pkts verify: 35
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0local crypto endpt.: 10.12.0.2, remote crypto endpt.: 1.1.1.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0xB7873D1E(3079093534)inbound esp sas:
spi: 0xE8738BE2(3899886562)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 39, flow_id: SW:39, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4595984/3495)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEinbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xB7873D1E(3079093534)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 40, flow_id: SW:40, crypto map: Virtual-Access1-head-0
sa timing: remaining key lifetime (k/sec): (4595985/3495)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEoutbound ah sas:
outbound pcp sas:
interface: FastEthernet0/0
Crypto map tag: MYMAP, local addr 2.2.2.2protected vrf: (none)
local ident (addr/mask/prot/port): (7.0.0.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (5.0.0.0/255.255.255.0/0/0)
current_peer 10.12.0.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 98, #pkts encrypt: 98, #pkts digest: 98 #pkts decaps: 98, #pkts decrypt: 98, #pkts verify: 98
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 1, #recv errors 0local crypto endpt.: 2.2.2.2, remote crypto endpt.: 10.12.0.1
path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/0
current outbound spi: 0x419146C7(1100039879)inbound esp sas:
spi: 0xEFAA9897(4020934807)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 41, flow_id: SW:41, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4378766/3562)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEinbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x419146C7(1100039879)
transform: esp-3des esp-sha-hmac ,
in use settings ={Tunnel, }
conn id: 42, flow_id: SW:42, crypto map: MYMAP
sa timing: remaining key lifetime (k/sec): (4378766/3562)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVEoutbound ah sas:
outbound pcp sas:
R2# show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
1.1.1.1 10.12.0.2 QM_IDLE 1017 0 ACTIVE 10.12.0.1 2.2.2.2 QM_IDLE 1018 0 ACTIVER2# show crypto isakmp sa detail
Codes: C - IKE configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal
X - IKE Extended Authentication
psk - Preshared key, rsig - RSA signature
renc - RSA encryption
IPv4 Crypto ISAKMP SAC-id Local Remote I-VRF Status Encr Hash Auth DH Lifetime Cap.
1017 10.12.0.2 1.1.1.1 ACTIVE 3des sha rsig 2 23:57:32 CX
Engine-id:Conn-id = SW:171018 2.2.2.2 10.12.0.1 ACTIVE 3des sha psk 2 23:59:12
Engine-id:Conn-id = SW:18
Thanks again to all who posted ideas.
I did a drawing from all the people who contributed, and the winner of the 50 rack tokens to our preferred rack vendor Graded Labs goes to Nick! Congratulations Nick, please email me privately and send me the email address that you use for your INE account, and I will have the tokens credited to your account. Again, thanks to all for all your contributions!
Keep up the great studies, hang in there, and never surrender.
P.S. Bob says "thank you" ;)
Best wishes.