CCIE Security - Tunnels within Tunnels challenge.
The two engineers, as they grabbed a quick lunch, looked over the following diagram.

The 13.0.0.0/24 network is GRE. The routing in place, uses the tunnel interfaces to reach the remote networks of 1.1.1.0 and 3.3.3.0. The IPSec policy is to encrypt all GRE traffic between R1 and R3. R1 and R3 are peering with each other using loopback 11 and loopback 33 respectively.
The technicians considered the traffic pattern if a host on the 3.3.3.0/24 network sent a packet to a device on the 1.1.1.0/24 network.
Then they reviewed the configurations (below), and discussed them. Based on what they saw, they just couldn’t agree completely with each other regarding the following questions?
1. How many IP headers would be in each packet.
2. What would the source and destination address be of each IP header.
3. What order the IP headers would be in (beginning with the outside header).
4. Would the IPSec be using transport or tunnel mode.
5. Would this be called IPSec over GRE, GRE over IPSec, or something else, (like "nightmare").
So they called for the expert, YOU, to assist in these questions.
Are you up to the challenge. Answering even 1 of them will be appreciated, so take moment now, and GO FOR IT !
Post your ideas, and we will put all the people who post ideas into a virtual hat, and draw a winner to receive 100 rack tokens to our preferred lab gear provider, graded labs. Please have your posts in by
the end of the day Monday, May24, 2010 to be in the drawing.
UPDATE:
It is May 24 - 2010. Here are the answers:
How many IP headers would be in each packet?
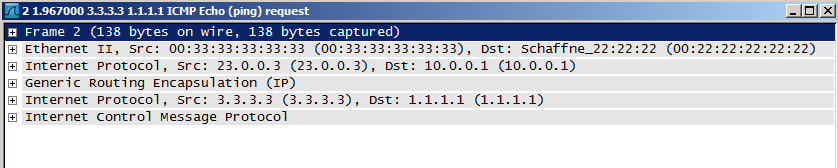
3 headers total. 1 outside header between the IPsec peers, and 2 encrypted headers in the ESP payload. (I used host addresses of 1.1.1.1 and 3.3.3.3 in the ping testing.)
What would the source and destination address be of each IP header?
1. source 33.33.33.3 destination 11.11.11.1
2. source 23.0.0.3 destination 10.0.0.1
3. source 3.3.3.3 destination 1.1.1.1
What order the IP headers would be in (beginning with the outside header)?
Using the numbering above:
1=Outside (just before ESP)
2=IP header, used for transporting the GRE, which is now being encrypted by ESP
3=Original IP header, buried deep in the encrypted packed.
Without encryption, the packet would look like this:

With encryption, it would look like this:

Would the IPSec be using transport or tunnel mode?
Tunnel. Because the crypto ACL included IP addresses outside of the endpoints of the tunnel, the peers will negotiate and use tunnel mode, (even though we administratively configured transport mode on the transform-sets).
This would be called GRE over IPSec, as in “GRE traffic, being carried over the network by IPSec”.
Thanks to everyone who responded!
We put all who contributed (anything at all) into a hat and drew a name. The winner of the 100 rack tokens is: Kingsley Charles ! (Please email me directly, and I will get the tokens for you. My email address is kbarker@ine.com)
The full configs for R1 and R3 are below, as well as a couple show commands to assist in your final determination.
Best wishes.
R1#show run
hostname R1
!
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set MYSET esp-des esp-md5-hmac
mode transport
!
crypto map MYMAP local-address Loopback11
crypto map MYMAP 10 ipsec-isakmp
set peer 33.33.33.3
set transform-set MYSET
match address 100
!
interface Loopback0
ip address 1.1.1.1 255.255.255.0
ip rip advertise 60
!
interface Loopback11
ip address 11.11.11.1 255.255.255.0
ip rip advertise 60
!
interface Tunnel0
ip address 13.0.0.1 255.255.255.0
tunnel source FastEthernet0/0
tunnel destination 23.0.0.3
!
interface FastEthernet0/0
ip address 10.0.0.1 255.255.255.0
ip rip advertise 60
duplex auto
speed auto
crypto map MYMAP
!
router rip
timers basic 60 90 90 90
network 10.0.0.0
network 11.0.0.0
!
ip route 3.0.0.0 255.0.0.0 Tunnel0
!
access-list 100 permit gre any any
endR1#show ip route | begin resort
Gateway of last resort is not set1.0.0.0/24 is subnetted, 1 subnets
C 1.1.1.0 is directly connected, Loopback0
R 2.0.0.0/8 [120/1] via 10.0.0.2, 00:00:27, FastEthernet0/0
R 33.0.0.0/8 [120/2] via 10.0.0.2, 00:00:27, FastEthernet0/0
S 3.0.0.0/8 is directly connected, Tunnel0
R 23.0.0.0/8 [120/1] via 10.0.0.2, 00:00:27, FastEthernet0/0
10.0.0.0/24 is subnetted, 1 subnets
C 10.0.0.0 is directly connected, FastEthernet0/0
11.0.0.0/24 is subnetted, 1 subnets
C 11.11.11.0 is directly connected, Loopback11
13.0.0.0/24 is subnetted, 1 subnets
C 13.0.0.0 is directly connected, Tunnel0
R1#R1#show crypto map
Crypto Map: "MYMAP" idb: Loopback11 local address: 11.11.11.1Crypto Map "MYMAP" 10 ipsec-isakmp
Peer = 33.33.33.3
Extended IP access list 100
access-list 100 permit gre any any
Current peer: 33.33.33.3
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
MYSET,
}
Interfaces using crypto map MYMAP:
FastEthernet0/0R1#
******************************************************
******************************************************R3#show run
hostname R3
!
crypto isakmp policy 1
authentication pre-share
crypto isakmp key cisco address 0.0.0.0 0.0.0.0
!
!
crypto ipsec transform-set MYSET esp-des esp-md5-hmac
mode transport
!
crypto map MYMAP local-address Loopback33
crypto map MYMAP 10 ipsec-isakmp
set peer 11.11.11.1
set transform-set MYSET
match address 100
!
!
interface Loopback0
ip address 3.3.3.3 255.255.255.0
ip rip advertise 60
!
interface Loopback33
ip address 33.33.33.3 255.255.255.0
ip rip advertise 60
!
interface Tunnel0
ip address 13.0.0.3 255.255.255.0
tunnel source FastEthernet0/1
tunnel destination 10.0.0.1
!
interface FastEthernet0/1
ip address 23.0.0.3 255.255.255.0
ip rip advertise 60
duplex auto
speed auto
crypto map MYMAP
!
router rip
timers basic 60 90 90 90
network 23.0.0.0
network 33.0.0.0
!
ip route 1.0.0.0 255.0.0.0 Tunnel0
!
access-list 100 permit gre any any
!
line con 0
exec-timeout 0 0
privilege level 15
logging synchronous
line aux 0
line vty 0 4
privilege level 15
no login
!
!
endR3#
R3#show ip route | begin resort
Gateway of last resort is not setS 1.0.0.0/8 is directly connected, Tunnel0
R 2.0.0.0/8 [120/1] via 23.0.0.2, 00:00:48, FastEthernet0/1
33.0.0.0/24 is subnetted, 1 subnets
C 33.33.33.0 is directly connected, Loopback33
3.0.0.0/24 is subnetted, 1 subnets
C 3.3.3.0 is directly connected, Loopback0
23.0.0.0/24 is subnetted, 1 subnets
C 23.0.0.0 is directly connected, FastEthernet0/1
R 10.0.0.0/8 [120/1] via 23.0.0.2, 00:00:48, FastEthernet0/1
R 11.0.0.0/8 [120/2] via 23.0.0.2, 00:00:48, FastEthernet0/1
13.0.0.0/24 is subnetted, 1 subnets
C 13.0.0.0 is directly connected, Tunnel0R3#show crypto map
Crypto Map: "MYMAP" idb: Loopback33 local address: 33.33.33.3Crypto Map "MYMAP" 10 ipsec-isakmp
Peer = 11.11.11.1
Extended IP access list 100
access-list 100 permit gre any any
Current peer: 11.11.11.1
Security association lifetime: 4608000 kilobytes/3600 seconds
PFS (Y/N): N
Transform sets={
MYSET,
}
Interfaces using crypto map MYMAP:
FastEthernet0/1R3#ping 1.1.1.1 so lo 0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 3.3.3.3
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 128/152/180 ms
R3#