Shocking Ways Amazon Macie Can Make You a Better Bass Player
So you want to play bass like legendary Bootsy Collins? That takes a lot of practice. But how do you have time to play along with Bootsy when you are worried about sensitive data in your Amazon S3 buckets? Let's see what we can do.

So what is Amazon Macie? It is a fully managed data security and data privacy service from AWS which leverages pattern matching and machine learning to discover your sensitive data in AWS S3. In other words, AWS has built machine learning models for finding sensitive data in your S3 buckets. All you have to do is run the service. Please remember, an adequately configured S3 bucket can be safe for storing sensitive data, but first you need to ensure appropriate access policies are in place and that your organization only uses specified buckets for sensitive data. That is where Macie can help.
To put it simply, Amazon Macie does two significant things to free up time for bass practice:
- It identifies your buckets that are public, unencrypted, or shared outside your organization
- It processes your buckets for sensitive data
Amazon made some updates to the service in February 2021. They include:
- Cross-account scanning giving you a centralized view of customers who have many different accounts under their control.
- Focusing scans to particular object prefixes allowing you to restrict the scan to objects with specific leading prefixes.
- A 30-day free trial for S3 bucket level inventory, access control and encryption evaluation.
And (our favorite) better cost estimations before jobs are submitted.
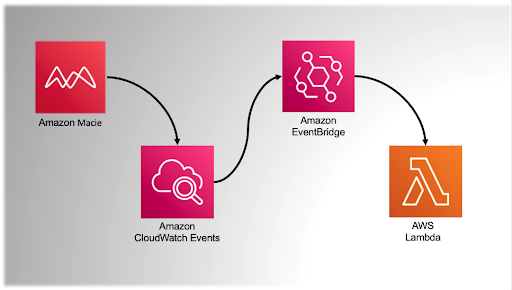
Like other AWS services, Macie is engineered to be used easily with other services. For example, you could set up a Macie scan, feed the results to CloudWatch, and then consume those results in a myriad of ways by other Amazon services. In the example below, Macie feeds results to an Amazon CloudWatch Events bus where a rule evaluates the results. If a match occurs, EventBridge routes to AWS Lambda for further processing such as triggering an alarm, updating a live console for operations, and so on. In short, if you are using AWS Security Hub you can configure Macie to publish all findings it creates to Security Hub. We found the documentation for this integration to be most useful, and you can check it out here: Amazon Macie integration with AWS Security Hub.
.Now that you know what Macie is, let's check out bucket identification by jumping into the Amazon Macie interface.
After enabling Macie in your AWS account, it will immediately run classification on your buckets.
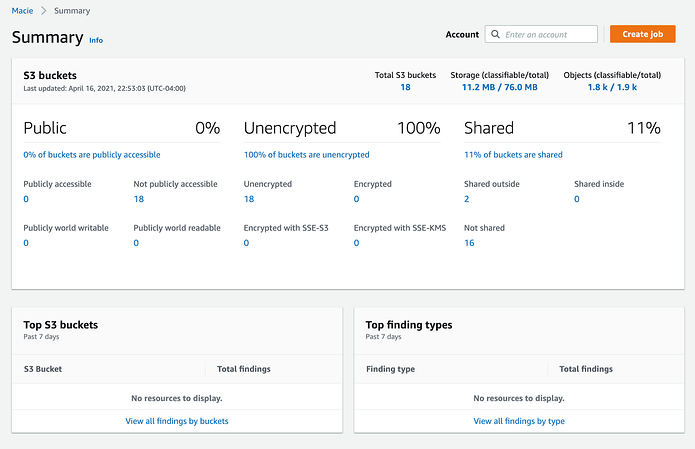
Here is a quick breakdown of what we see:
- Public 0%: No buckets in this account have an Identity and Access Management (IAM) policy that makes them publicly viewable. Since public accessibility is one of the top reasons for losing control of sensitive data in S3, if you have public buckets, get this under control ASAP! (See ProTip #2 below.)
- Unencrypted 100%: Hmmm? No S3 bucket under this organizational report has enabled encryption. That is a call for action, fellow bassists! Encrypting buckets and their contents requires a few clicks of the mouse and will not affect the rest of your infrastructure. Remember: encrypt wherever possible.
- Shared 11%: There is an IAM policy that has shared 11% of the buckets (in this case, 2). The interface makes it easy to identify these buckets by clicking the link under the finding. In this case, the link labeled 11% of buckets are shared.
With this information, here is a game plan to follow:
- If you have public folders, find out their status and why they are public. If you cannot get answers quickly, remove the public permission and wait to see who starts making noise. Security is serious business and should be treated as such.
- Encrypting a bucket is simple and easy, so unless there are mitigating circumstances, make it a policy. All you will need to do is click the link below the unencrypted section and start the inquiry.
- For shared buckets, you are looking for buckets shared outside your organization. This review could take a little more time since it might involve reviewing each bucket's policy.
- Enable notifications via AWS Config for public buckets.
ProTip #1: This page, and the information it contains, could be the basis of a solid data security status report. The summary page gives you a 40,000-foot view of your Amazon S3 buckets. With an acceptable template, you could quickly and easily issue a weekly or even daily report.
ProTip #2: AWS Config is your friend when it comes to public buckets. If your organization is using Config, and controlling the creation of public buckets is a concern, create a new rule using the AWS managed rule s3-bucket-public-read-prohibited. If a bucket is created with or modified to allow public read, this rule will fire.
The bucket review of our S3 buckets puts you a long, long way down the road to having a confident assessment of our security posture. But this is only half of the picture. The next step, ensure you know where sensitive data is stored. And that's what we will check out in our next AWS blog post. Until then, fire up your favorite Bootsy solo and slide off to a funktacular groove, friends.