Pentesting 101: Fingerprinting Continued

In the continuation of our Pentesting 101 series we dive deeper into fingerprinting. During the remainder of this series, we will display nmap screenshots. We recommend reading the command line switches here to familiarize yourself with the information before the next section of the article is released. It’s worth it to take a moment to read the command line switches on this page to familiarize yourself with the upcoming set of screenshots.
Need a refresher on our Fingerprinting 101 series? Catch up here.
Since we are trying to paint a picture of the target network, saving the nmap output would help. The command line switch “-oA” will output the results of a nmap scan to XML, a grepable format and plain text like you’d see on the screen. Also, since we are trying to gather as much information as possible, nmap should be used to scan all ports, pull back the banners of the services, get the version information of the service and finally the operating system information.
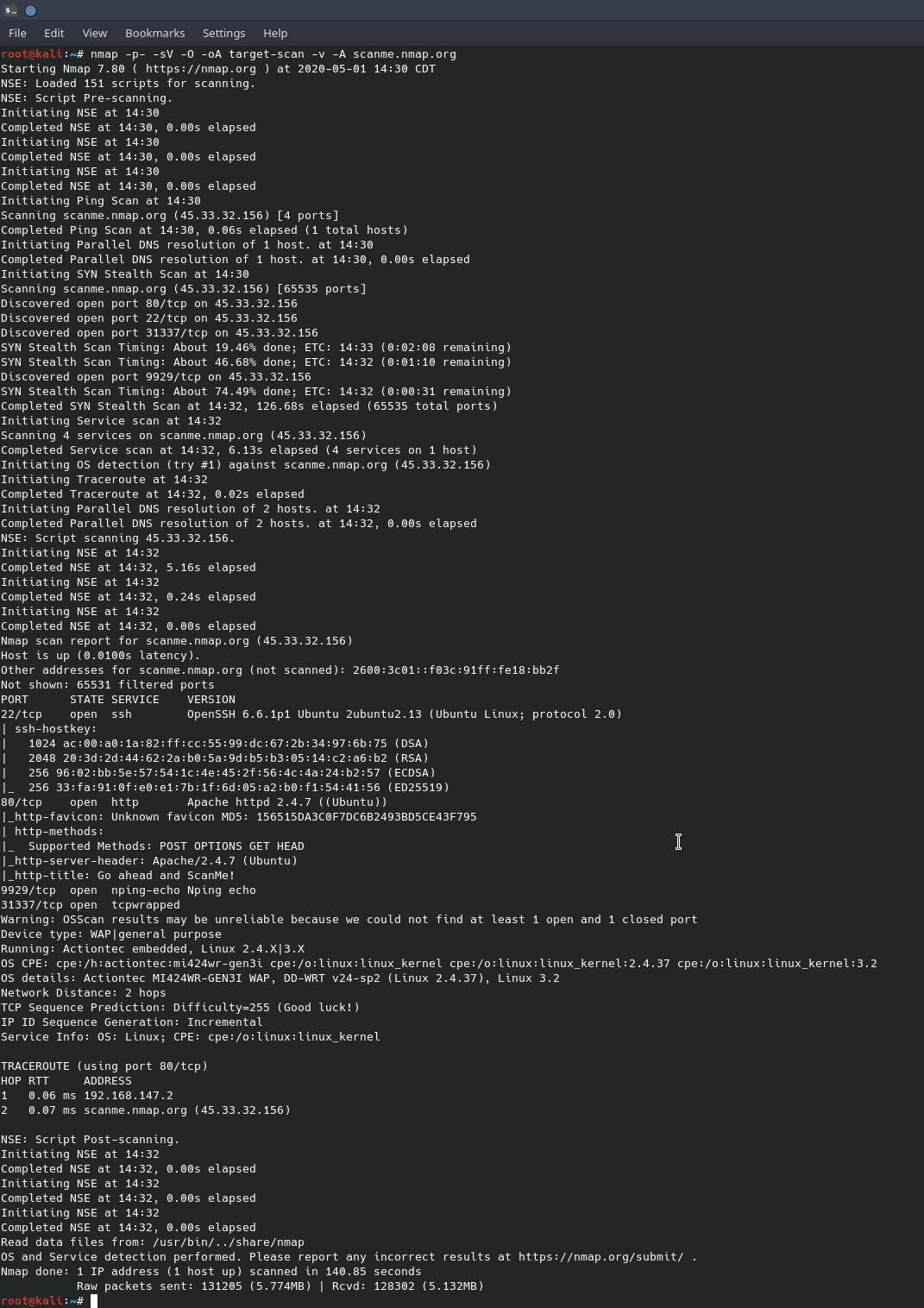
There is a lot of information in the above screenshot. Using the “-v” flag gives a verbose output. Since we saved the output of nmap, catting the file “target-scan.nmap” will show a more human readable scan output.
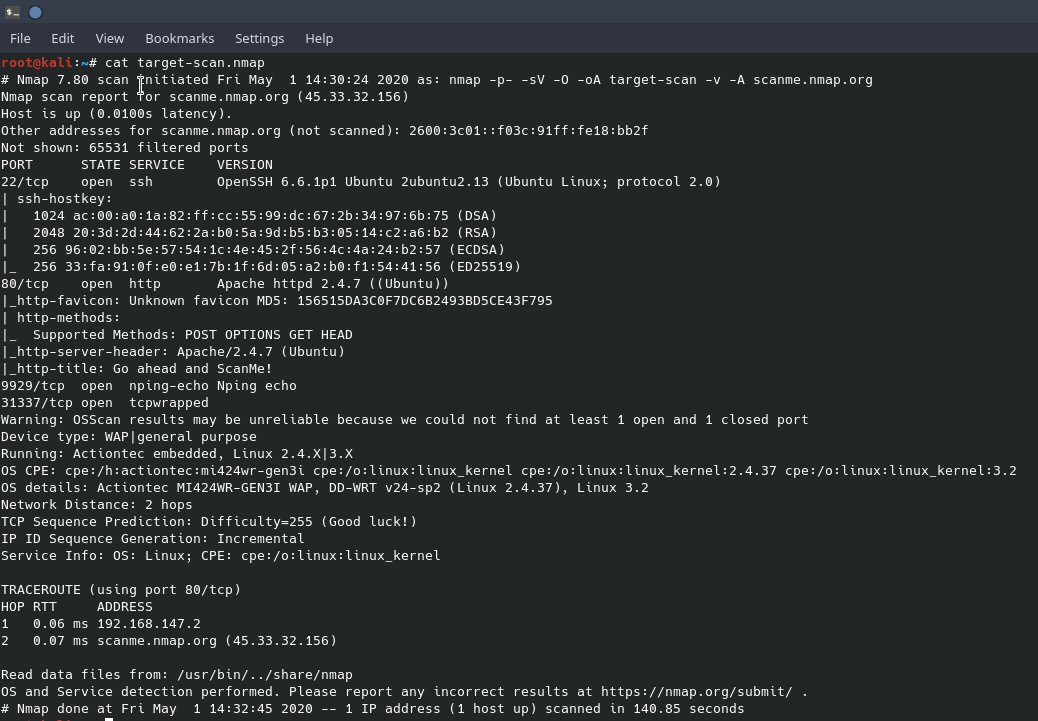
You’ll notice that the nmap file shows when the scan was run as well as the nmap options. This is great information that adds to the target information log. Breaking down the command line switches are; “-p-” which is shorthand for scan all ports, 0-65535, “-sV” to do a version scan of the services, “-O” to enable operating system detection, “-oA target-scan” for saving the scan to a file, “-v” for the verbose messages seen in nmap screenshot 2, and “-A” to enable operating system version detection and a traceroute. The nmap scan output shows OpenSSH is running on port 22 and the version is 6.66.1p1 and the Apache web server, version 2.4.7, is running on port 80. It appears that the operating system is an embedded Linux called DD-WRT running on an Actiontec MI424WR-GEN3I WAP. This information can be used as a starting block to finding an exploit against these services.
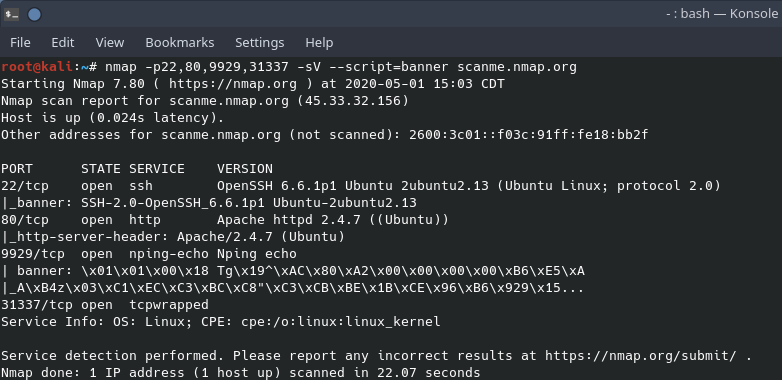
Extending nmap’s feature set is running scripts through the nmap scripting engine. Below is an example of using an nmap script to grab the banner of the open ports. Notice that ports 22 and 80 have human readable banners and ports 9929 and 31337 do not. Ordinarily these odd ports would be cause for more investigation but scanme.nmap.org is an example of how to use these tools and not a target for a penetration test.
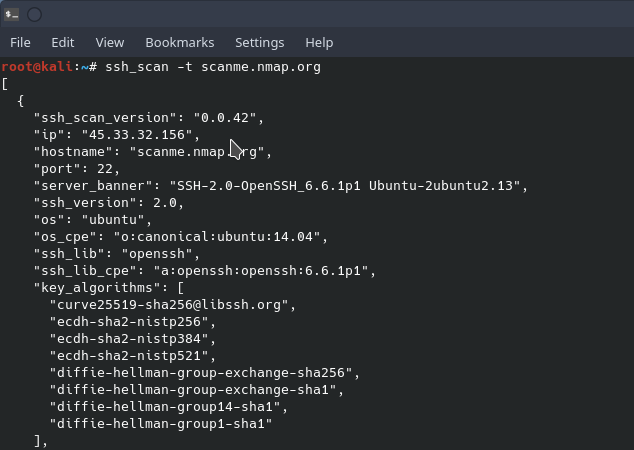
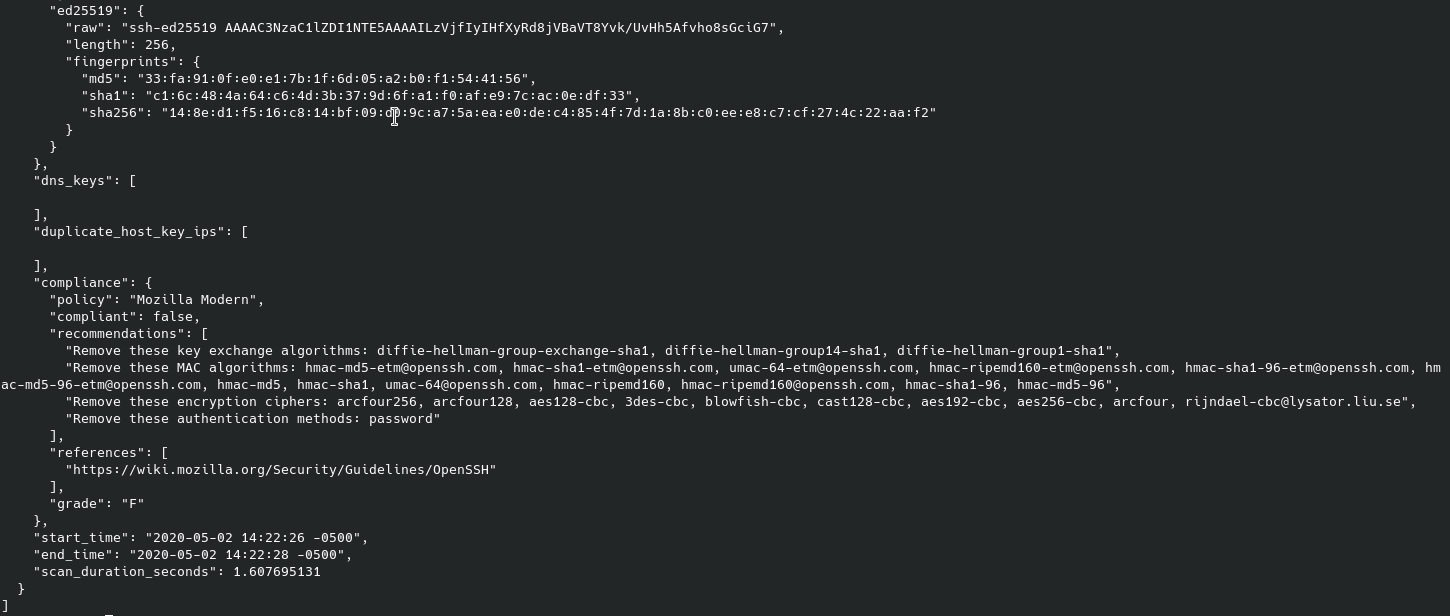
Now that we have a detailed port scan, we can narrow down our fingerprinting to services we would like to investigate. Starting off with port 22, nmap showed that OpenSSH was running. Using an ssh scanner will provide more information about the service and if it contains any vulnerabilities. One such scanner is the simple “ssh_scan.” ssh_scan is a simple program that enumerates the SSH service, shows authentication methods, encryption algorithms, and keys then prints its output to the screen in JSON format.
To gather information on a web server there are countless tools out there. One of those tools is called whatweb. Whatweb provides a simple output for the user about the targeted web server. It can also scan whole domains for web servers as well as the web server for various server features through the use of its 1800+ plugins.

Another tool in the arsenal of a penetration tester is Nikto. Nikto is a comprehensive web scanner that checks many different aspects of the server to include version information, subdomain enumeration and authentication, while also supporting SSL. Nikto also lists vulnerabilities found in the scanned web server as well as references to more information about the vulnerabilities.
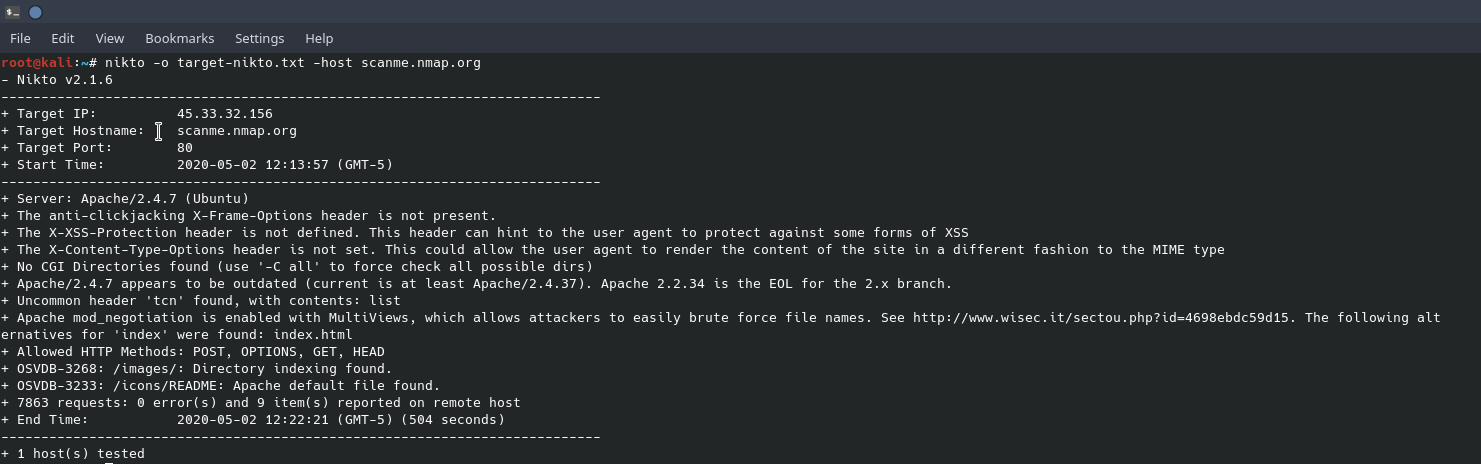
In the above screenshot you’ll notice a scan done by nikto against the target web server. By default, nikto scans with all plugins. The options the web server is using, how busy it is and if it has many vulnerabilities can affect how long a nikto scan takes. Nikto will also pull back the “robots.txt” file if the server is hosting one. The robots.txt file can lead to other places to scan on a web server. Using the command line flag of “-o”, we can send the output to a file and “-host” tells which host to scan. You’ll notice in one of the lines near the top it says “use ‘-C all’ to force check all possible dirs.” This option allows nikto to scan for common directories found on web servers. In our example, using “-C all” takes a considerable amount of time and does not yield many results. There are other tools available to the penetration tester that can scan a web server for files and directories in a more efficient manner than nikto.
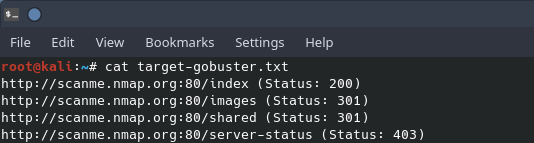
Gobuster is a multi-threaded web scanner that searches for directories and files. It is most commonly used to scan a web server for hidden directories via a provided wordlist. One of the more unique features of gobuster is that you can also use it to search for files by file extension. Gobuster uses HTTP status codes to identify if directories or files are present. Using gobuster can help uncover a login or administrative portal that isn’t advertised on the main page.
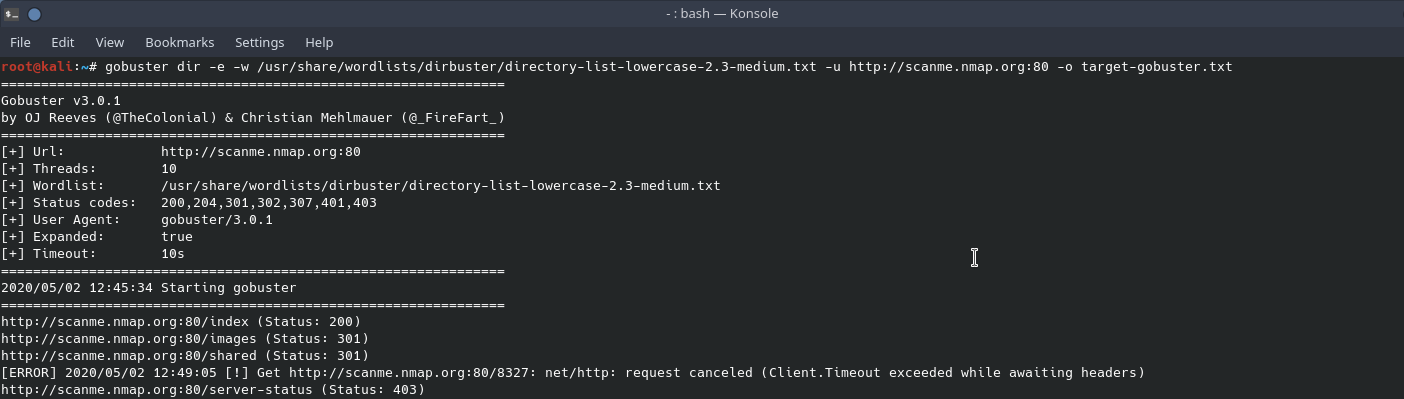
In the above example of gobuster, we used a dir search to scan for hidden directories on the server using the wordlist provided. The command line flag of “-e” says to show the expanded URL instead of the normal output of “/index”, etc. Catting the output file, we can see a cleaner output of what was found using gobuster. Depending on was found during the gobuster scan could be reason to look more into those hidden directories or files during a penetration test.